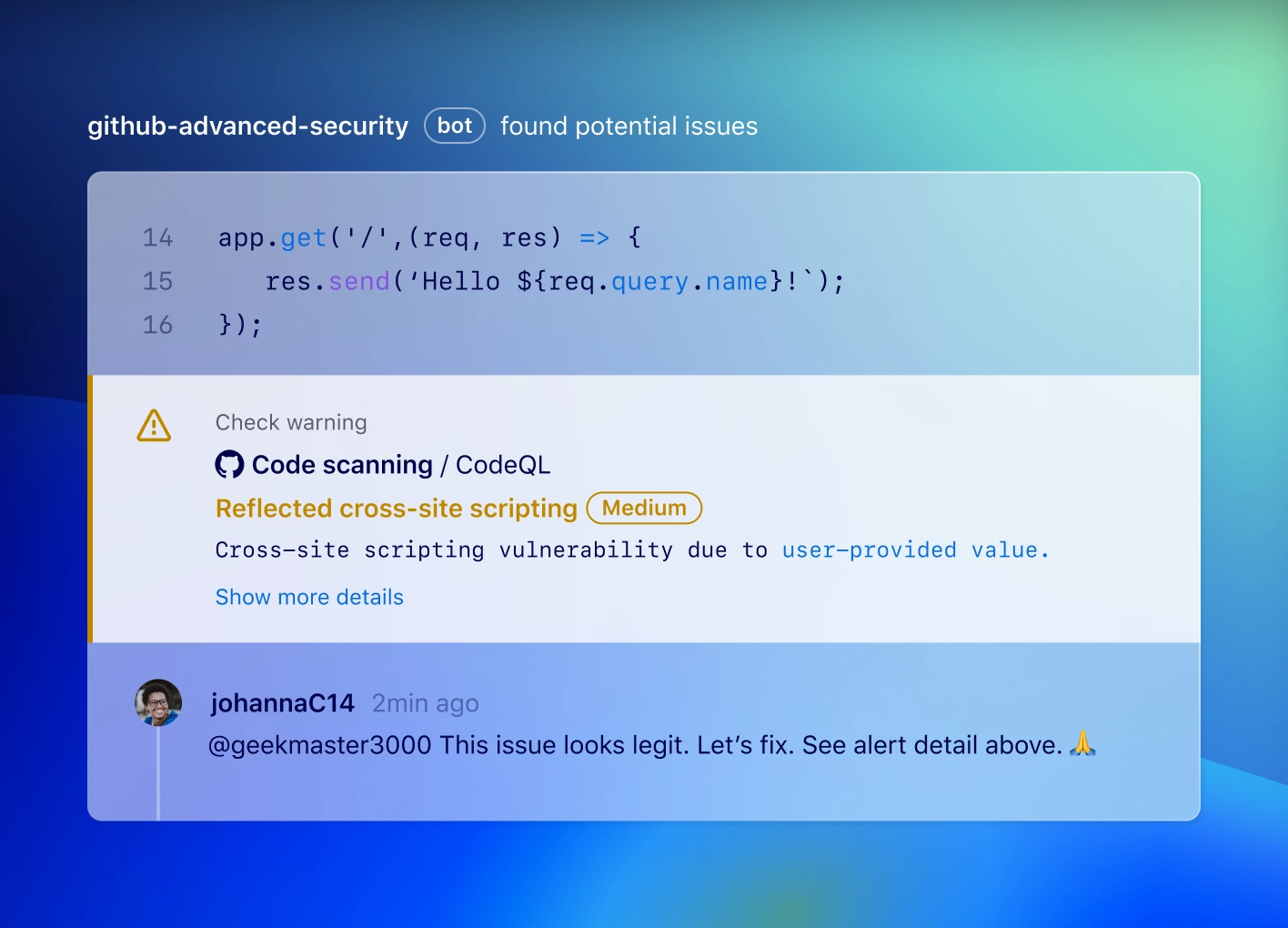
With actionable feedback in the pull request, code scanning helps you find, triage, and prioritize security vulnerabilities right in your workflow.

Application security
where found means fixed
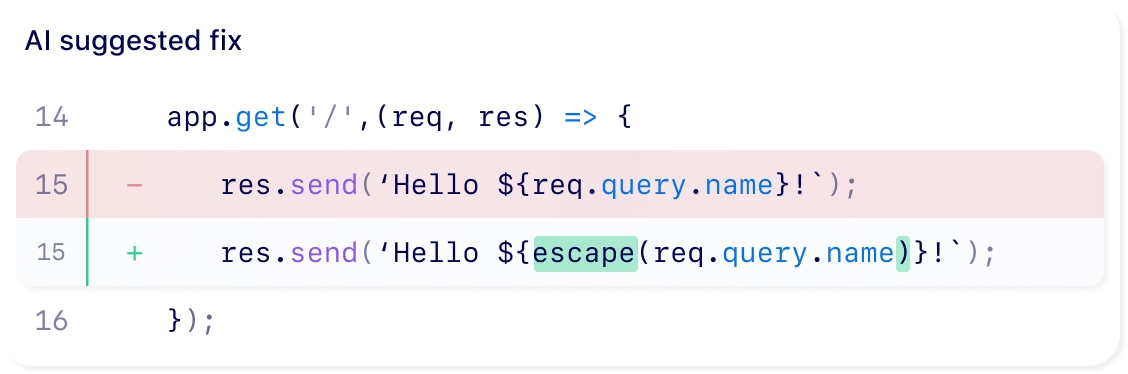
Powered by Copilot Autofix.
GitHub Security is used by
Fixes in minutes,
not months.
With AI-powered remediation, static analysis, secret scanning, and software composition analysis, GitHub Advanced Security helps developers and security teams work together to eliminate security debt and keep new vulnerabilities out of code.
Secure code, accelerated

Found means fixed
 GitHub Advanced Security helps developers fix potential issues before production.
GitHub Advanced Security helps developers fix potential issues before production.

For developers who love to code. Detect, prevent, and fix vulnerabilities without leaving your flow.
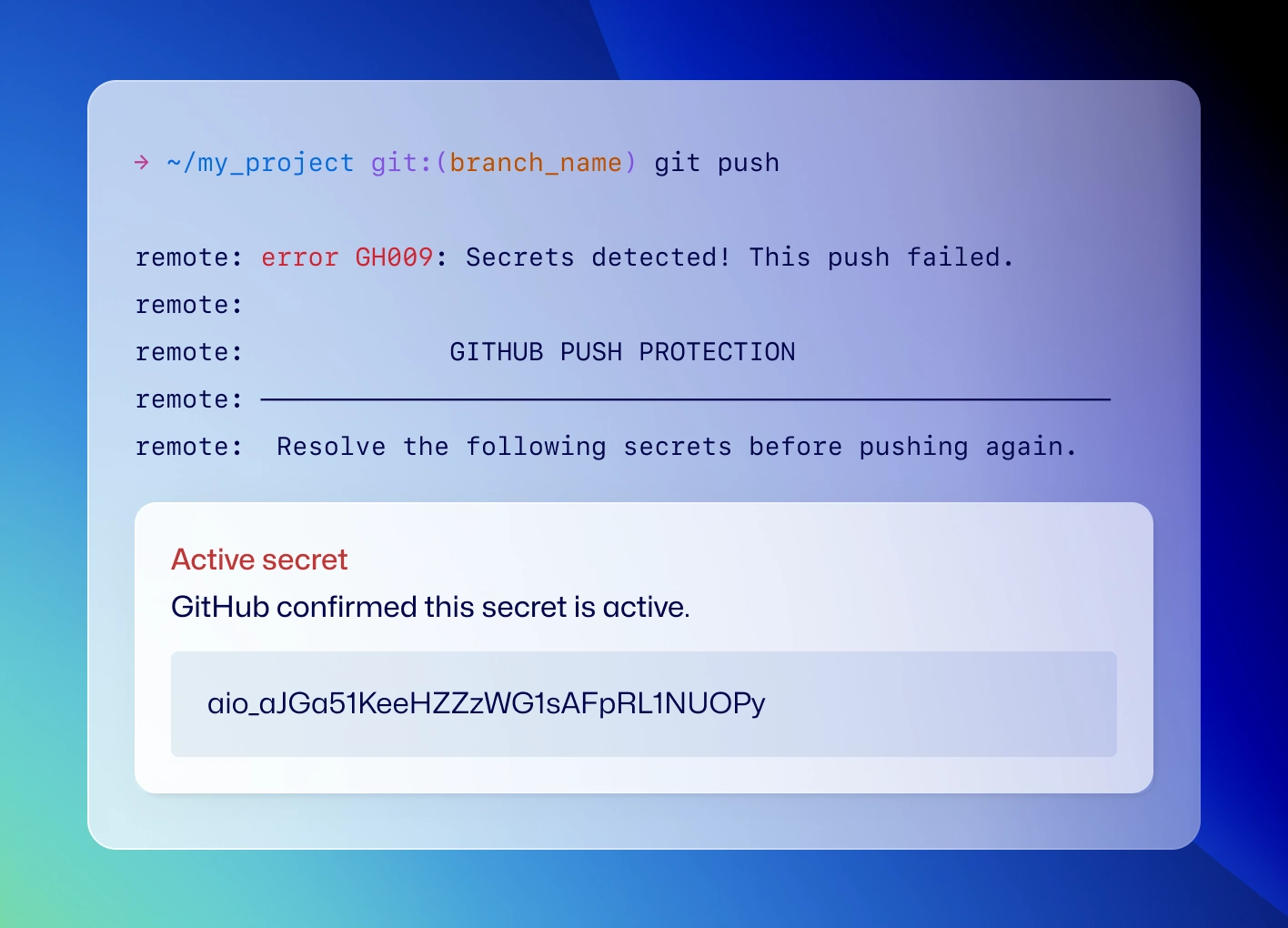
Push protection is such a beautiful workflow. We’ve never received a single complaint from developers.

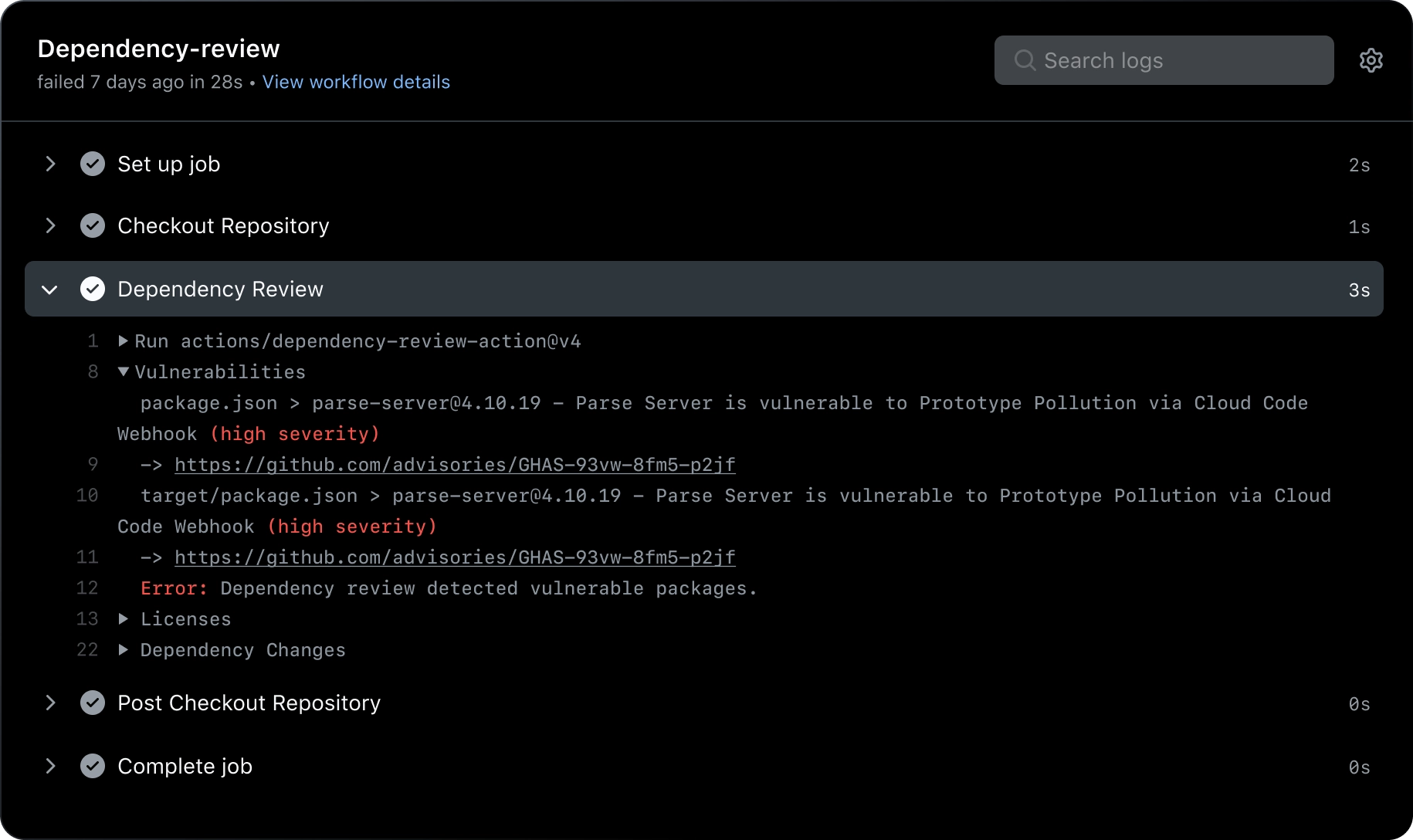
Dependencies you can depend on
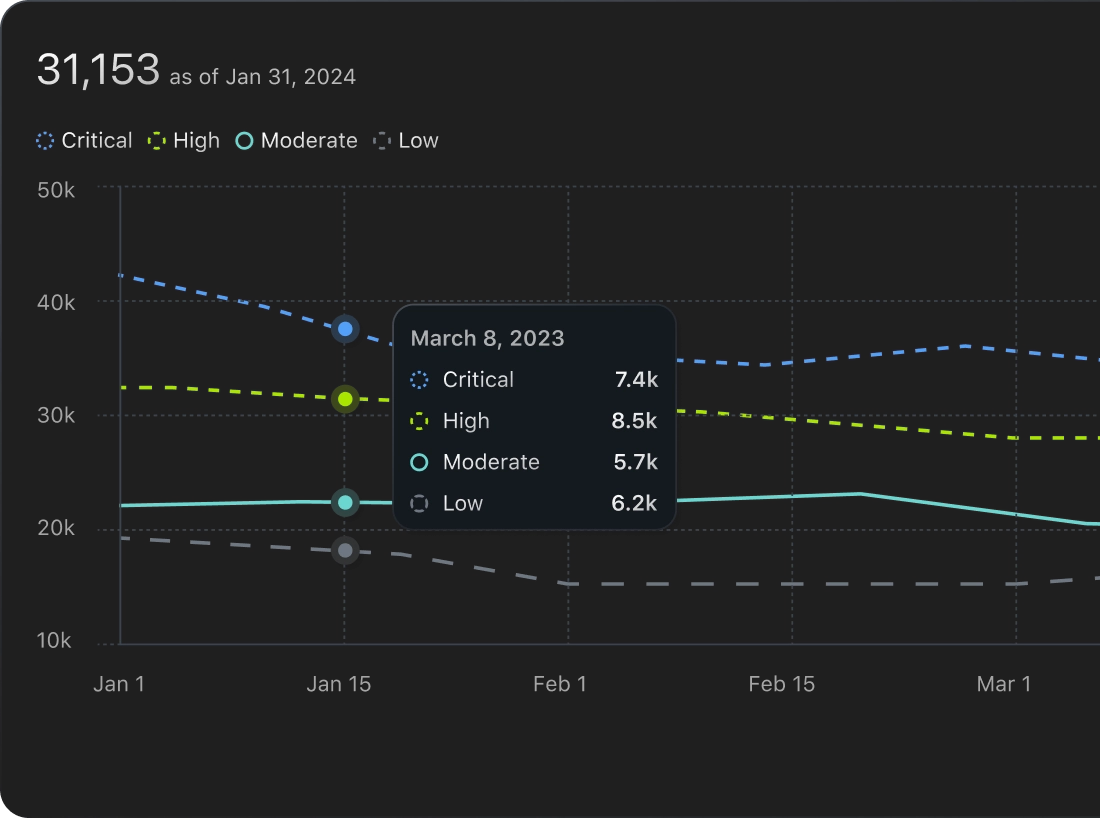
Security status at a glance
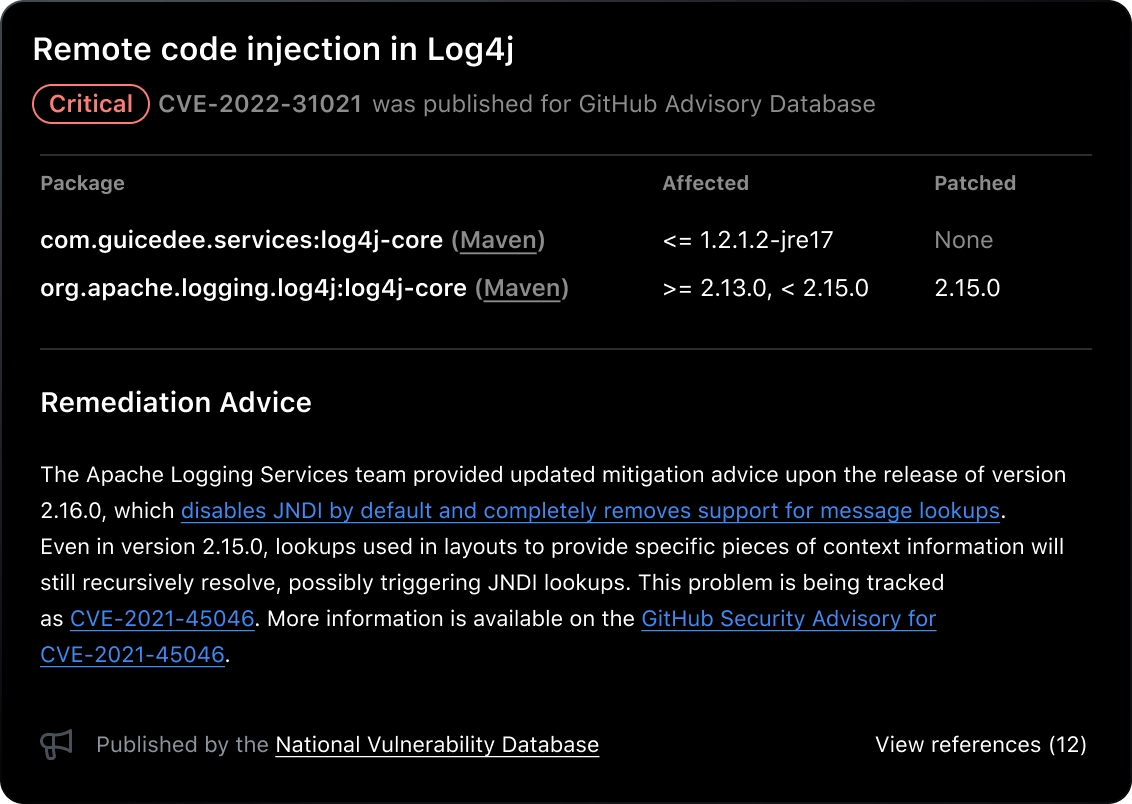
Your workflows,
your tools
Enable native security
for every repository
Eliminate toolchain cost and complexity with native DevSecOps tools for
GitHub Enterprise and Azure DevOps.
Standard security
Manage and secure open source components and public repositories
- Included, Code scanning for public repositories
- Not included, Copilot Autofix**
- Not included, Autofixes in pull requests and for existing alerts
- Not included, Contextual vulnerability intelligence and advice
- Not included, Hunt zero-day threats and their variants
- Included, Find secrets in public repositories only
- Included, Block secrets on pushes to public repositories
- Not included, Revoke and notify on leaked secrets
- Not included, Copilot Secret Scanning**
- Not included, Find elusive secrets like PII and passwords**
- Included, Identify and update vulnerable open source components
- Included, Access intelligence in the GitHub Advisory Database
- Included, Report vulnerabilities to open source maintainers
- Included, Generate and export SBOMs
- Included, Manage transitive dependencies with submission API
- Included, Detect calls to vulnerable functions (public repositories)
- Not included, Define and enforce auto-triage rules
- Not included, View security metrics and insights
- Not included, Assess feature adoption and code security risk
- Not included, Enable security features for multiple repositories
GitHub Advanced Security
Detect, prevent, and remediate vulnerabilities in all public and private repositories
- Included, Code scanning for private and public repositories
- Included, Copilot Autofix**
- Included, Autofixes in pull requests and for existing alerts
- Included, Contextual vulnerability intelligence and advice
- Included, Hunt zero-day threats and their variants
- Included, Find secrets in public and private repositories
- Included, Block secrets on pushes to public and private repositories
- Included, Revoke and notify on leaked secrets
- Included, Copilot Secret Scanning**
- Included, Find elusive secrets like PII and passwords**
- Included, Identify and update vulnerable open source components
- Included, Access intelligence in the GitHub Advisory Database
- Included, Report vulnerabilities to open source maintainers
- Included, Generate and export SBOMs
- Included, Manage transitive dependencies with submission API
- Included, Detect calls to vulnerable functions (all repositories)
- Included, Define and enforce auto-triage rules
- Included, View security metrics and insights
- Included, Assess feature adoption and code security risk
- Included, Enable security features for multiple repositories
Get the most out of
GitHub Advanced Security
Frequently Asked Questions
General
What is GitHub Advanced Security?
GitHub Advanced Security is the native Static Application Security Testing (SAST) solution for GitHub Enterprise and Azure DevOps. Designed to accelerate the delivery of secure software, GitHub Advanced Security adds cutting-edge tools for static analysis, software composition analysis, and secret scanning to the GitHub platform that developers already know and love. Unlike traditional application security packages that burden the software development toolchain with complex workflows that inhibit adoption, GitHub Advanced Security makes it easy for developers to find and fix vulnerabilities earlier in the software development life cycle. By adding GitHub Advanced Security to the GitHub platform, security leaders can address compliance requirements while empowering development teams to solve customer problems, surpass competitors, and reduce the time-to-value for software development projects.
Why choose GitHub Advanced Security instead of a third-party AppSec product?
Unlike third-party security add-ons, GitHub Advanced Security operates entirely in the native GitHub workflows that developers already know and love. By making it easier for developers to remediate vulnerabilities as they go, GitHub Advanced Security frees time for security teams to focus on critical strategies that protect businesses, customers, and communities from application-based vulnerabilities.
What is DevSecOps?
DevSecOps refers to a combination of the development, security, and operations tools necessary to develop software applications.
What is AppSec?
Application security (AppSec) is the process of finding, fixing, and preventing security vulnerabilities in applications. GitHub Advanced Security provides AppSec tools for static application security testing (SAST), which identifies vulnerabilities in the code itself. Unlike dynamic application security testing (DAST), which probes live applications for vulnerabilities, GitHub Advanced Security helps keep vulnerabilities out of production.
Where can I find information about the security of the GitHub platform?
The GitHub platform itself features multiple layers of security to keep developers and their code safe in transit and at rest.
Evaluation
Which GitHub plans are compatible with GitHub Advanced Security?
GitHub Advanced Security can be added to GitHub Enterprise Cloud (GHEC) and GitHub Enterprise Server (GHES) plans. If you have a free or Team account, you will need to upgrade to a GitHub Enterprise plan before you can add GitHub Advanced Security. You can also request a free trial of both GitHub Enterprise and GitHub Advanced Security; contact sales to learn more.
Can I use GitHub Advanced Security with Microsoft Azure DevOps?
Yes. GitHub Advanced Security is available as an add-on for Azure DevOps.
Can I get a demo or a free trial of GitHub Advanced Security?
Yes. Please contact sales to request a free trial.
Where can I find a video overview of GitHub Advanced Security?
This video provides an overview of GitHub Advanced Security, plus demos of key features like code scanning, AI-powered autofix code suggestions, software supply chain management, and secret scanning.
Where can I find case studies and reference customers?
Read our customer stories to learn how customers like Telus, Mercado Libre, and KPMG use GitHub Advanced Security to secure applications and accelerate the software development lifecycle.
AI
What are the AI-powered features in GHAS?
Copilot Autofix explains vulnerabilities in code and provides code suggestions to speed remediation. In addition, AI is used to find elusive secrets like passwords, and generate custom patterns so secret scanning can identify sensitive data like personally identifying information (PII) based on natural-language examples.
What languages does Copilot Autofix support?
Copilot Autofix can generate explanations and code suggestions for all languages supported by the CodeQL code scanning engine, including C++, C#, Go, Java, JavaScript/Typescript, Kotlin, Ruby, and Swift.
Do I need to purchase a GitHub Copilot license?
No. Copilot Autofix is exclusive to and included with GitHub Advanced Security. A Copilot license is not required.
Deployment
Can I review documentation before purchase?
Yes. As with all GitHub products, documentation for GitHub Advanced Security is publicly available.
Does GitHub offer consulting, training, and other deployment services?
Yes! Please visit Expert Services to learn more.
More Security Resources
What security features are free to use for public repositories?
As part of our mission to support the open source community and keep open source software safe and reliable for all, GitHub provides security features like code scanning, secret scanning, and supply chain security tools at no charge for use with public repositories.
What is the GitHub Security Lab?
The GitHub Security Lab is a team of security experts who cultivate a collaborative community where developers and security professionals come together to help secure open source software. Our mission: make open source software secure and reliable for the benefit of developers everywhere through collaboration and contributions from maintainers, developers, and security researchers around the world.
What is the Advisory Database, and how is it different from a CVE?
Common Vulnerabilities and Exposures (CVE) is a database of publicly disclosed information about security issues, with a unique number to identify each vulnerability. But while CVEs document vulnerabilities, they don’t tell the whole story. Unlike a CVE, entries in the GitHub Advisory Database contain additional context and remediation guidance – sourced from a global community of security experts and curated by the GitHub Security Lab – to help developers and security teams understand vulnerabilities, assess risk, and fix with confidence.
How can I manage and secure open source dependencies?
GitHub provides extensive supply chain security tools and resources to help developers and maintainers keep open source software up-to-date and secure, including Dependabot. If you’re new to software supply chain security, the Dependabot quickstart guide is a great place to begin.
General
What is GitHub Advanced Security?
GitHub Advanced Security is the native Static Application Security Testing (SAST) solution for GitHub Enterprise and Azure DevOps. Designed to accelerate the delivery of secure software, GitHub Advanced Security adds cutting-edge tools for static analysis, software composition analysis, and secret scanning to the GitHub platform that developers already know and love. Unlike traditional application security packages that burden the software development toolchain with complex workflows that inhibit adoption, GitHub Advanced Security makes it easy for developers to find and fix vulnerabilities earlier in the software development life cycle. By adding GitHub Advanced Security to the GitHub platform, security leaders can address compliance requirements while empowering development teams to solve customer problems, surpass competitors, and reduce the time-to-value for software development projects.
Why choose GitHub Advanced Security instead of a third-party AppSec product?
Unlike third-party security add-ons, GitHub Advanced Security operates entirely in the native GitHub workflows that developers already know and love. By making it easier for developers to remediate vulnerabilities as they go, GitHub Advanced Security frees time for security teams to focus on critical strategies that protect businesses, customers, and communities from application-based vulnerabilities.
What is DevSecOps?
DevSecOps refers to a combination of the development, security, and operations tools necessary to develop software applications.
What is AppSec?
Application security (AppSec) is the process of finding, fixing, and preventing security vulnerabilities in applications. GitHub Advanced Security provides AppSec tools for static application security testing (SAST), which identifies vulnerabilities in the code itself. Unlike dynamic application security testing (DAST), which probes live applications for vulnerabilities, GitHub Advanced Security helps keep vulnerabilities out of production.
Where can I find information about the security of the GitHub platform?
The GitHub platform itself features multiple layers of security to keep developers and their code safe in transit and at rest.
Evaluation
Which GitHub plans are compatible with GitHub Advanced Security?
GitHub Advanced Security can be added to GitHub Enterprise Cloud (GHEC) and GitHub Enterprise Server (GHES) plans. If you have a free or Team account, you will need to upgrade to a GitHub Enterprise plan before you can add GitHub Advanced Security. You can also request a free trial of both GitHub Enterprise and GitHub Advanced Security; contact sales to learn more.
Can I use GitHub Advanced Security with Microsoft Azure DevOps?
Yes. GitHub Advanced Security is available as an add-on for Azure DevOps.
Can I get a demo or a free trial of GitHub Advanced Security?
Yes. Please contact sales to request a free trial.
Where can I find a video overview of GitHub Advanced Security?
This video provides an overview of GitHub Advanced Security, plus demos of key features like code scanning, AI-powered autofix code suggestions, software supply chain management, and secret scanning.
Where can I find case studies and reference customers?
Read our customer stories to learn how customers like Telus, Mercado Libre, and KPMG use GitHub Advanced Security to secure applications and accelerate the software development lifecycle.
AI
What are the AI-powered features in GHAS?
Copilot Autofix explains vulnerabilities in code and provides code suggestions to speed remediation. In addition, AI is used to find elusive secrets like passwords, and generate custom patterns so secret scanning can identify sensitive data like personally identifying information (PII) based on natural-language examples.
What languages does Copilot Autofix support?
Copilot Autofix can generate explanations and code suggestions for all languages supported by the CodeQL code scanning engine, including C++, C#, Go, Java, JavaScript/Typescript, Kotlin, Ruby, and Swift.
Do I need to purchase a GitHub Copilot license?
No. Copilot Autofix is exclusive to and included with GitHub Advanced Security. A Copilot license is not required.
Deployment
Can I review documentation before purchase?
Yes. As with all GitHub products, documentation for GitHub Advanced Security is publicly available.
Does GitHub offer consulting, training, and other deployment services?
Yes! Please visit Expert Services to learn more.
More Security Resources
What security features are free to use for public repositories?
As part of our mission to support the open source community and keep open source software safe and reliable for all, GitHub provides security features like code scanning, secret scanning, and supply chain security tools at no charge for use with public repositories.
What is the GitHub Security Lab?
The GitHub Security Lab is a team of security experts who cultivate a collaborative community where developers and security professionals come together to help secure open source software. Our mission: make open source software secure and reliable for the benefit of developers everywhere through collaboration and contributions from maintainers, developers, and security researchers around the world.
What is the Advisory Database, and how is it different from a CVE?
Common Vulnerabilities and Exposures (CVE) is a database of publicly disclosed information about security issues, with a unique number to identify each vulnerability. But while CVEs document vulnerabilities, they don’t tell the whole story. Unlike a CVE, entries in the GitHub Advisory Database contain additional context and remediation guidance – sourced from a global community of security experts and curated by the GitHub Security Lab – to help developers and security teams understand vulnerabilities, assess risk, and fix with confidence.
How can I manage and secure open source dependencies?
GitHub provides extensive supply chain security tools and resources to help developers and maintainers keep open source software up-to-date and secure, including Dependabot. If you’re new to software supply chain security, the Dependabot quickstart guide is a great place to begin.
- Overall, the median time for developers to use Copilot Autofix to automatically commit the fix for a PR-time alert was 28 minutes, compared to 1.5 hours to resolve the same alerts manually (3x faster). For SQL injection vulnerabilities: 18 minutes compared to 3.7 hours (12x faster). Based on new code scanning alerts found by CodeQL in pull requests (PRs) on repositories with GitHub Advanced Security enabled. These are examples; your results will vary.
- A Comparative Study of Software Secrets Reporting by Secret Detection Tools, Setu Kumar Basak et al., North Carolina State University, 2023